Here’s a detailed guide to the Top 10 Cybersecurity Threats in 2025 and how to defend against them. As technology evolves, cyber threats are becoming more sophisticated and harder to detect. From ransomware attacks to deepfake scams, businesses and individuals face growing cybersecurity challenges. To protect yourself in 2025, it’s essential to understand these threats and adopt the right security practices.
Table of Contents
1. Ransomware Attacks

What It Is:
Malware that encrypts your data and demands a ransom to unlock it. Attackers often target businesses, healthcare institutions, and individual users. Ransomware is among the Top 10 Cybersecurity Threats in 2025, affecting both individuals and organizations.
How to Stay Safe:
- Regularly back up your data on secure, offline storage.
- Use advanced antivirus and endpoint protection solutions.
- Never click on suspicious links or download unverified files.
2. Phishing Attacks

What It Is:
Cybercriminals trick victims into revealing sensitive information through fake emails, messages, or websites. Phishing is one of the Top 10 Cybersecurity Threats in 2025, with spear phishing becoming increasingly targeted and dangerous.
How to Stay Safe:
- Verify the sender’s email address and URL before clicking on links.
- Use multi-factor authentication (MFA) for added security.
- Deploy email filtering tools to detect phishing attempts.
3. Deepfake Scams

What It Is:
AI-generated fake videos or audio clips that impersonate real people, often used for fraud, misinformation, or blackmail. Deepfake scams are a rising concern among the Top 10 Cybersecurity Threats in 2025, with serious implications for privacy and security.
How to Stay Safe:
- Be cautious with unexpected video calls or voice requests involving financial transactions.
- Use tools to detect deepfakes.
- Verify any unusual request through another secure channel.
4. Internet of Things (IoT) Vulnerabilities

What It Is:
Smart devices like cameras, thermostats, and appliances can be exploited if they lack proper security. IoT vulnerabilities rank among the Top 10 Cybersecurity Threats in 2025, as more homes and businesses adopt connected devices.
How to Stay Safe:
- Change default passwords on all IoT devices.
- Keep firmware updated.
- Use a separate network for smart devices.
5. Supply Chain Attacks

What It Is:
Hackers compromise a trusted third-party service or software update to gain access to a company’s network. Supply chain attacks are listed in the Top 10 Cybersecurity Threats in 2025, especially for businesses relying on external vendors.
How to Stay Safe:
- Vet third-party vendors for security compliance.
- Monitor network activity for unusual behavior.
- Apply security patches and updates promptly.
Read:
How to Create and Manage a Database: A Comprehensive Guide for Professionals
6. Cloud Security Risks

What It Is:
With more businesses moving to the cloud, vulnerabilities in cloud storage and misconfigured services are becoming a common target. Cloud security risks are part of the Top 10 Cybersecurity Threats in 2025, impacting data privacy and business operations.
How to Stay Safe:
- Implement strong access controls and encryption.
- Regularly audit cloud security configurations.
- Use zero-trust security models.
7. Credential Stuffing Attacks
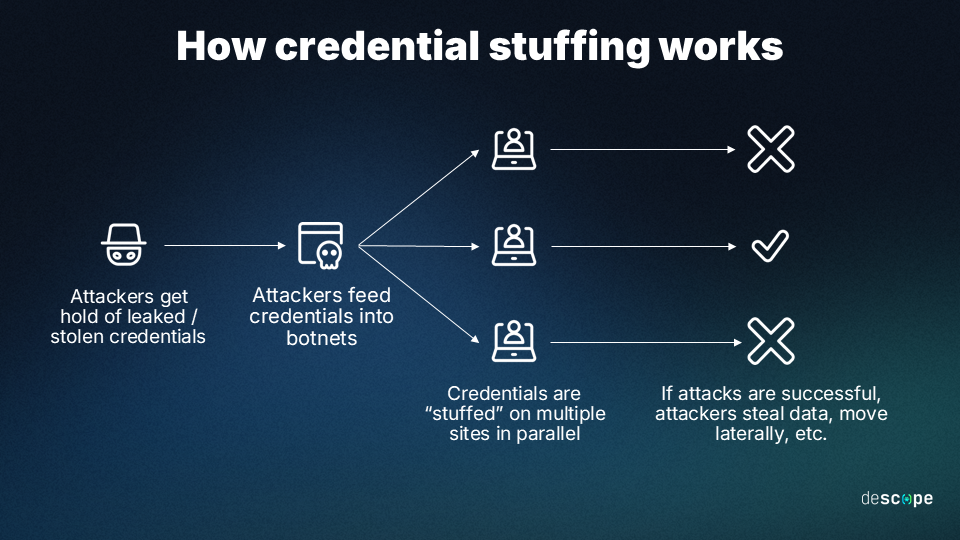
What It Is:
Hackers use stolen username-password combinations from data breaches to gain access to other accounts. Credential stuffing attacks make it into the Top 10 Cybersecurity Threats in 2025, taking advantage of reused passwords.
How to Stay Safe:
- Use unique passwords for each account.
- Enable multi-factor authentication.
- Regularly check if your credentials are exposed on breach-monitoring services like Have I Been Pwned.
8. Social Engineering Attacks
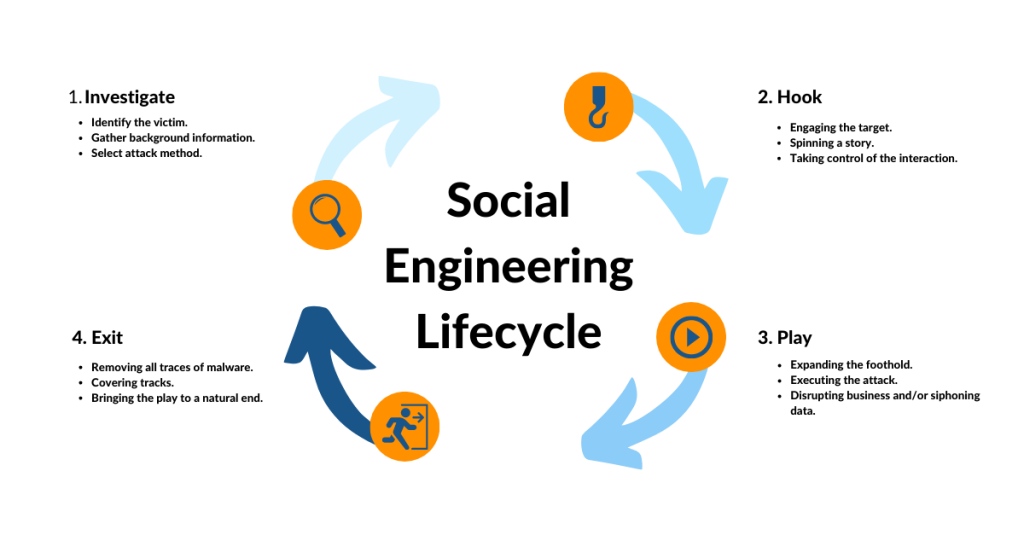
What It Is:
Manipulating individuals into divulging confidential information through psychological tactics rather than technical methods. Social engineering attacks remain a key part of the Top 10 Cybersecurity Threats in 2025, as they rely on human error.
How to Stay Safe:
- Be skeptical of unsolicited requests for personal information.
- Educate employees on social engineering tactics.
- Use security awareness training programs.
9. Zero-Day Vulnerabilities
What It Is:
Exploits for software vulnerabilities that are unknown to the vendor, making them difficult to detect and patch. Zero-day vulnerabilities are among the Top 10 Cybersecurity Threats in 2025, requiring constant vigilance and rapid response.
How to Stay Safe:
- Keep all software updated.
- Use advanced threat detection solutions.
- Employ intrusion prevention systems (IPS).
10. Cryptocurrency Scams

What It Is:
Cybercriminals use fake investment schemes, phishing, or malware to steal cryptocurrency from users. Cryptocurrency scams round out the Top 10 Cybersecurity Threats in 2025, as digital currencies become more mainstream.
How to Stay Safe:
- Avoid unsolicited investment offers.
- Use hardware wallets for cryptocurrency storage.
- Enable two-factor authentication on all crypto-related accounts.
Best Practices for Staying Safe in 2025
- Use Strong Passwords and a Password Manager: Never reuse passwords, and use a reliable password manager for added security.
- Enable Multi-Factor Authentication (MFA): Add an extra layer of protection to your accounts.
- Regular Security Updates: Keep your operating system, apps, and firmware up to date.
- Secure Your Network: Use a firewall, VPN, and secure Wi-Fi network.
- Security Awareness Training: Educate yourself and your team about the latest cyber threats.
Conclusion
Cybersecurity threats are evolving, but by staying informed and implementing proactive measures, you can protect yourself and your organization. Make sure to adopt these security practices to reduce your vulnerability in 2025 and beyond.
Learn More:
Top 10 Smart Gadgets for Home Automation in 2025
CGPA Calculator: The Easiest Way to Calculate Your Cumulative GPA











